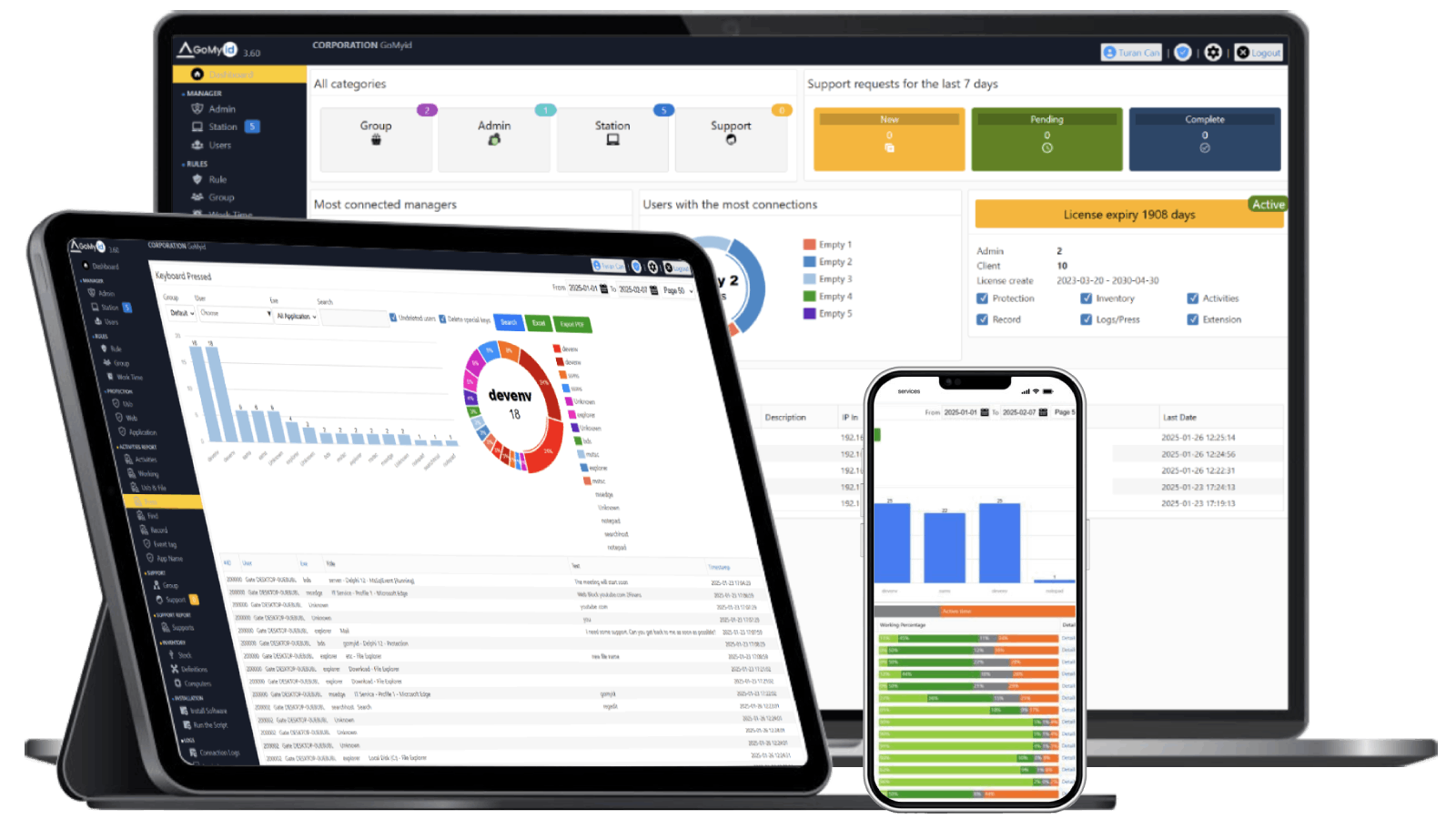
Understanding Employee Monitoring software in Modern Enterprises
Modern enterprises operate in increasingly complex digital environments. Distributed teams, remote access, regulatory pressures, and rising cybersecurity threats have transformed employee monitoring software from a managerial tool into a strategic IT function. self-hosted employee monitoring software for Modern Enterprises is designed to address these challenges while aligning with enterprise-grade security and privacy standards.
Evolution of Workforce Management Technologies
Early monitoring software tools focused primarily on attendance and basic activity logging. Today, enterprise solutions integrate deeply with operating systems, networks, and internal policies. This evolution reflects the need for visibility across digital workflows without sacrificing trust, compliance, or performance.
Why Monitoring Is a Strategic IT Function
For IT departments, monitoring is no longer about surveillance. It is about safeguarding systems, ensuring acceptable use, identifying risks early, and maintaining operational continuity. Enterprises now demand solutions that provide insight while respecting employee privacy and organizational governance.
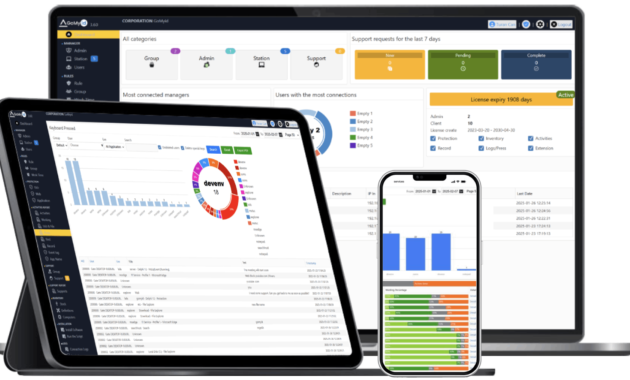
What Is Self-Hosted Employee Monitoring Software?
Definition and Core Architecture
Self-hosted employee monitoring software is deployed entirely within an organization’s own infrastructure. All components—data collection, storage, processing, and reporting—operate on local servers or private networks. This architecture eliminates reliance on third-party cloud services.
In the context of Self-Hosted Employee Monitoring Software for Modern Enterprises, this model ensures that sensitive workforce data never leaves the organization’s controlled environment.
Self-Hosted vs Cloud-Based Monitoring Solutions
Cloud-based tools often promise convenience, but they introduce trade-offs. Data is stored externally, subject to third-party access, cross-border transfers, and shared infrastructure risks. Self-hosted solutions, by contrast, give enterprises full visibility and control over every layer of the monitoring software.
Privacy-First Architecture: A Core Enterprise Requirement
Data Residency and Regulatory Alignment
Regulations such as GDPR, HIPAA, and sector-specific compliance frameworks place strict requirements on how employee data is collected, stored, and processed. A privacy-first architecture ensures data residency remains within approved geographic and legal boundaries.
Self-hosted monitoring aligns naturally with these requirements, allowing enterprises to define retention policies, access controls, and audit mechanisms internally.
Minimizing Risk Through Local Data Processing
By keeping data on-premise, organizations reduce exposure to external breaches, vendor misuse, or unexpected policy changes. Privacy-first design also supports transparency, helping enterprises maintain employee trust while meeting legal obligations.
Full Data Ownership and On-Premise Control
Why Enterprises Demand Total Data Sovereignty
Data sovereignty is no longer optional for large organizations. Monitoring data can include application usage, system events, and behavioral patterns—information that must be protected as rigorously as financial or customer data.
Self-Hosted Employee Monitoring Software for Modern Enterprises ensures that ownership of this data remains exclusively with the organization.
Infrastructure-Level Governance and Security
On-premise control allows IT teams to apply existing security frameworks, such as network segmentation, role-based access, and internal encryption standards. Monitoring systems become part of the broader enterprise security posture rather than an external dependency.
Introducing DeskGate: An On-Premise Monitoring Platform
DeskGate’s Technical Overview
DeskGate is a self-hosted, on-premise employee monitoring software solution designed specifically for enterprise environments. It operates entirely within local infrastructure, with no mandatory cloud components. Data is collected from endpoints and processed on internal servers under direct IT supervision.
Designed for Enterprise IT Environments
DeskGate integrates with existing authentication systems, internal networks, and compliance workflows. Its architecture reflects enterprise priorities: stability, scalability, security, and privacy. By avoiding cloud dependency, DeskGate supports organizations that require strict control over their digital assets.
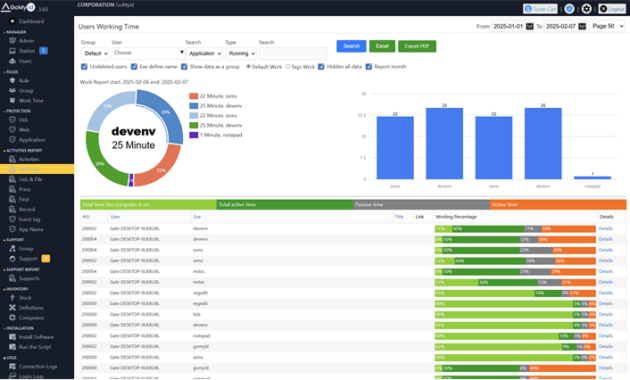
Key Use Cases for Modern Organizations
IT Departments and System Oversight
For IT teams, DeskGate provides visibility into system usage, application behavior, and operational patterns. This insight supports troubleshooting, capacity planning, and early detection of anomalies without exposing data externally.
Remote and Hybrid Workforce Management
As remote work becomes standard, enterprises need tools that ensure productivity and security beyond the office perimeter. Self-hosted monitoring enables oversight of remote endpoints while maintaining consistent security policies across locations.
Internal Compliance and Policy Enforcement
DeskGate supports internal audits, acceptable use policies, and compliance reporting. Because all data remains local, compliance teams can conduct reviews without involving third-party vendors or risking unauthorized data access.
No Cloud Dependency: Benefits of Local Infrastructure
Reduced Attack Surface
Eliminating cloud connectivity reduces the number of external access points attackers can exploit. On-premise systems operate behind corporate firewalls, benefiting from existing intrusion detection and prevention mechanisms.
Performance, Latency, and Reliability
Local infrastructure offers predictable performance and low latency. Enterprises are not affected by internet outages, vendor downtime, or bandwidth constraints. Monitoring continues uninterrupted, even in isolated or high-security environments.
Implementation Considerations for Enterprises
Deployment Models and Scalability
Self-hosted solutions like DeskGate can be deployed in centralized data centers or distributed across regional offices. Enterprises can scale the system according to workforce size and infrastructure capacity, maintaining performance without sacrificing control.
Integration With Existing IT Ecosystems
Successful deployment depends on compatibility with directory services, endpoint management tools, and security platforms. DeskGate is designed to complement existing enterprise ecosystems rather than replace them.
FAQs: Self-Hosted Employee Monitoring Software for Modern Enterprises
1. Is self-hosted employee monitoring suitable for large organizations?
Yes. It is particularly well-suited for large enterprises that require scalability, compliance, and strict data governance.
2. How does DeskGate support employee privacy?
DeskGate uses a privacy-first architecture, keeping all data on-premise and allowing organizations to define transparent monitoring policies.
3. Does self-hosted monitoring work for remote teams?
Absolutely. Endpoints can be monitored securely regardless of location, as long as they connect to the organization’s network.
4. What industries benefit most from on-premise monitoring?
Industries with strict compliance requirements—such as finance, healthcare, government, and technology—benefit significantly.
5. Is cloud connectivity required at any stage?
No. DeskGate operates without mandatory cloud dependency, ensuring full local control.
6. How does this approach support internal compliance?
By keeping data local, compliance audits and investigations can be conducted securely and efficiently.
Conclusion: The Future of Enterprise Monitoring
As enterprises navigate complex regulatory, security, and workforce challenges, Self-Hosted Employee Monitoring Software for Modern Enterprises represents a strategic shift toward control, transparency, and trust. Solutions like DeskGate demonstrate that effective monitoring does not require sacrificing privacy or data ownership.
By adopting a self-hosted, privacy-first approach with full on-premise control, modern enterprises can support IT operations, remote teams, and compliance initiatives—while maintaining sovereignty over one of their most valuable assets: data.